January 22nd, 2024 by Function4
Leading Managed Technology Services Provider (MTSP) Delivers Innovative
“Dual Claim Coverage” Model to Minimize Wait Time and Eliminate Hassle
SUGAR LAND, TX ‐ Function4, a leading managed technology
services provider (MTSP), announced today they’ve...
Read Full Story »
Tags: cyber insurance, cyberattacks, data backup
Posted in: Press Release
December 18th, 2023 by Function4
Cyber security is not a luxury but a necessity for any business that operates in the digital world. Cyber-attacks are an ever-present and evolving threat that can cause severe damage to your business in the form of data breaches, financial losses,...
Read Full Story »
Tags: cyber risks, cyber security, cyberattacks
Posted in: Cybersecurity
November 1st, 2023 by Function4
In the ever-evolving landscape of cybersecurity threats, businesses face a multitude of risks that can compromise sensitive data, tarnish their reputation, and lead to financial losses.
One of the most ominous and hidden corners of the internet...
Read Full Story »
Tags: cyber security, cyberattacks, dark web
Posted in: Cybersecurity
September 1st, 2023 by Function4
In today's digitally connected world, safeguarding your sensitive information and maintaining the security of your digital assets is of paramount importance.
Cyberattacks and data breaches can devastate businesses and individuals, leading to...
Read Full Story »
Tags: cyber risks, cyber security, cyberattacks
Posted in: Cybersecurity
May 5th, 2023 by Function4
This article provides valuable insights into the challenges of navigating cyber insurance claims and offers effective solutions to mitigate risks.
With the increasing prevalence of cyber threats, cyber insurance has become a critical component...
Read Full Story »
Tags: cyber insurance, cyber risks, cyber security, cyberattacks
Posted in: Cybersecurity
April 26th, 2023 by Function4
A comprehensive cyber-security assessment is an evaluation of a system's security posture that identifies vulnerabilities and measures the effectiveness of existing countermeasures. It typically includes a full review of hardware and software, as well...
Read Full Story »
Tags: cyber security, cyberattacks, network security, phishing, security, solutions
Posted in: Cybersecurity
April 19th, 2023 by Function4
Leading MTSP Protects Small to Mid-Sized Businesses from Ransomware Attacks
SUGAR LAND, TX – Function4, a leading managed technology services
provider (MTSP), announced today that the company has launched a Ransomware-as-a-Service...
Read Full Story »
Tags: cyber security, cyberattacks, managed IT, network security, phishing, ransomware, services, solutions
Posted in: Press Release
April 10th, 2023 by Function4
The world of technology has created an entirely new type of security issue for school districts: cyber threats. These attacks can come in many forms, from phishing scams to ransomware, and can have a devastating impact on school districts. Not only...
Read Full Story »
Tags: antivirus, cyber security, cyberattacks, education, phishing, ransomware, school
Posted in: Cybersecurity
April 5th, 2023 by Function4
Leading MTSP Combines Cybersecurity Experts with State-of-the-Art Technology
Sugar Land, TX – Function4, a leading managed technology services provider (MTSP) is protecting SMBs (small to mid-sized businesses) from cyberattacks through their...
Read Full Story »
Tags: cyber security, cyberattacks, security, services, solutions
Posted in: Cybersecurity, Business Technology, Press Release, IT Services
April 4th, 2023 by Function4
Dark web monitoring is a specialized form of cyber security designed to help organizations detect and respond to
threats that are hidden in the dark corners of the internet. By using advanced technology and
intelligence-gathering methods,...
Read Full Story »
Tags: cyber security, cyberattacks, dark web, security, services, solutions
Posted in: Cybersecurity, IT Services
March 20th, 2023 by Kevin Box
Cybersecurity is an increasingly important issue for organizations, as cyber-attacks become more frequent, sophisticated, and dangerous. Every organization needs to take proactive steps to protect their networks and data from external threats. In this...
Read Full Story »
Tags: cyber security, cyberattacks, ransomware, services
Posted in: Cybersecurity
February 7th, 2023 by Ed Hoffmann
Cyber insurance is an essential component of a comprehensive risk management strategy for businesses of all sizes. It provides financial protection against losses and liability arising from cyber-attacks, data breaches, and other cybersecurity incidents....
Read Full Story »
Tags: cyber security, cyberattacks, education, tips & training
Posted in: Cybersecurity
January 26th, 2023 by Function4
There are many reasons for the increase in cyber-attacks on businesses. One reason is that businesses increasingly use computer networks and the internet to conduct their operations. This provides more opportunities for hackers to gain access to sensitive...
Read Full Story »
Tags: antivirus, cyber security, cyberattacks, managed IT, ransomware, services, solutions
Posted in: Cybersecurity
January 17th, 2023 by Kevin Box
Over the last few years, we've seen Information security spend increase at historical levels which is estimated to cost organizations more than $172 billion by the end of 2022 according to Gartner. Now, it seems a new threat is lurking by way of the...
Read Full Story »
Tags: cyber security, cyberattacks, data collection, services, solutions
Posted in: Cybersecurity
January 3rd, 2023 by Kevin Box
I've outlined in recent articles the vulnerabilities of printers on the network. To expand on this topic, we need to focus on the vulnerabilities of why this is the case and what are the best practices in fixing the problem. In this article, we will...
Read Full Story »
Tags: antivirus, cyber security, cyberattacks, IoT, managed IT, services
Posted in: Cybersecurity
December 27th, 2022 by Kevin Box
Prior to COVID, printer fleets were mostly hybrid, meaning organizations deployed both larger workgroup copiers in specific locations around their office to maximize employee usage with some select employees having a desktop printer on their desk. After...
Read Full Story »
Tags: cyber security, cyberattacks, multifunction printers (MFP), printing, solutions
Posted in: Managed Print Services
December 27th, 2022 by Function4
Network monitoring provides a comprehensive view of the health and performance of your IT infrastructure. This helps you in identifying and troubleshooting any issues, as well as helping to maintain optimal network performance for maximum efficiency....
Read Full Story »
Tags: antivirus, cyber security, cyberattacks, managed IT, ransomware
Posted in: IT Services
December 8th, 2022 by Function4
Dark web scanning is particularly important for businesses because of the potential risk posed by data breaches. The dark web is a collection of websites and networks that are not indexed by search engines, making it difficult to detect or monitor...
Read Full Story »
Tags: cyberattacks, dark web, managed IT, risk management, services, solutions
Posted in: Cybersecurity
November 30th, 2022 by Function4
There are many tools and topics that everyone should know about cyber security, and we will be sharing details about them in this article. Here are ten topics everyone should know about cyber security:
Business Email Compromise (BEC)
BEC...
Read Full Story »
Tags: antivirus, cyber security, cyberattacks, dark web, data backup and recovery, passwords, ransomware, services
Posted in: Cybersecurity
October 26th, 2022 by Bill Patsouras
Leading Managed Technology Services
Provider Invests in Advanced
Cybersecurity Tools
SUGAR LAND, TX – Function4, a leading managed technology services provider (MTSP), has increased their investments in an advanced cybersecurity technology...
Read Full Story »
Tags: cyber security, cyberattacks, managed IT, SaaS
Posted in: Cybersecurity, Press Release
October 12th, 2022 by Function4
Leading Provider in Managed IT
Services Shares Best Practices for
Dealing with Data Attacks
Through DNS
SUGAR LAND, TX – Function4 a leading managed
technology services provider
(MTSP), is helping small to mid-sized...
Read Full Story »
Tags: cyber security, cyberattacks, managed IT, services, small & medium-sized businesses (SMB)
Posted in: Press Release
October 3rd, 2022 by Cherrie Cole
Don’t be forced to walk the plank with your supplies.
The work phone rings. You answer with the company name. The person on the other side says, “Hi, I am [a made-up name] we service your copier and need you to verify the...
Read Full Story »
Tags: copier services, cyberattacks, managed IT, multifunction printers (MFP)
Posted in: Cybersecurity
September 8th, 2022 by Function4
Leading MTSP Shares Why Email Is an Easy Way to Destroy A Company’s Network
SUGAR LAND, TX - Function4, a leading managed technology services provider (MTSP), recently announced that they are protecting small to mid-sized businesses (SMBs) with...
Read Full Story »
Tags: cyber security, cyberattacks, email, services, solutions
Posted in: Press Release
August 29th, 2022 by Kevin Box
Your organization is continuously creating confidential, valuable data that's critical to it running optimally and efficiently in real-time. And you're probably using multiple security methods–including authentication, encryption, and monitoring–to...
Read Full Story »
Tags: antivirus, copier services, cyber security, cyberattacks, risk management, solutions
Posted in: Cybersecurity, Managed Print Services
July 25th, 2022 by Function4
The modern world is a world of computers and technology. Over the years, we have flourished and achieved outstanding accomplishments in many aspects, and technology is one of them.
However, while technology has flourished, so has the prevalence...
Read Full Story »
Tags: antivirus, cyber security, cyberattacks, data backup and recovery, ransomware, risk management
Posted in: Cybersecurity
March 17th, 2022 by Function4
Leading MTSP Shares Most Common Cause of Cyberattacks and How to Secure Any Organization
SUGAR LAND, TX – February 25, 2022 - Function4 a leading managed technology services provider (MTSP), is protecting customers from the leading cause of cyberattacks...
Read Full Story »
Tags: cyber security, cyberattacks, passwords
Posted in: Cybersecurity, Press Release
September 30th, 2021 by Function4
Leading Managed Technology
Services Provider (MTSP) Leverages
Innovative Wireless Access Points to
Secure Connections to the Internet
SUGAR LAND, TX - Function4, a leading managed
technology services provider
(MTSP), announced today that the...
Read Full Story »
Tags: cyber security, cyberattacks, wifi
Posted in: Press Release
August 30th, 2021 by Function4
Leading Managed Technology Services
Provider Keeps SMBs Safe, Once
Again
SUGARLAND, TX Function4, a leading managed
technology services provider (MTSP),
recently shared that their robust
cybersecurity solutions have protected
their customers...
Read Full Story »
Tags: cyber security, cyberattacks, ransomware
Posted in: Press Release
August 10th, 2021 by Kevin Box
On April 29th, 2021, Cyber Criminals were able to hack the largest fuel pipeline in the U.S. because of one password floating around on the dark web, which an employee had previously used to access the organizations' network through a Virtual Private...
Read Full Story »
Tags: cyberattacks, multifunction printers (MFP), risk management
Posted in: Cybersecurity
July 30th, 2021 by Function4
Leading Managed Technology Services
Provider Shares How SMBs Can
Protect Themselves from Cyberattacks
and Ransomware Threats
SUGARLAND, TX Function4, a leading
managed technology services
provider (MTSP), recently
shared that some of the nation's...
Read Full Story »
Tags: cyber security, cyberattacks, data backup and recovery
Posted in: Press Release
July 29th, 2021 by Neville M. Bilimoria
The recent events of the Colonial Pipeline gas shortage in the Southeast have highlighted a very real concern for our nation’s cybersecurity. Cyber criminals are still out there, and seemingly stronger than ever.
But in our representation...
Read Full Story »
Tags: cyberattacks, healthcare, HIPAA / PHI
Posted in: Cybersecurity
July 20th, 2021 by Gabriela Garner
Security breaches create significant problems for any organization. They tax resources, put your reputation in danger and, most of all, cost money. Healthcare organizations are especially vulnerable to security breaches and often have the most to...
Read Full Story »
Tags: cyberattacks, encryption, healthcare, HIPAA / PHI, multifunction printers (MFP), content & process management
Posted in: Cybersecurity
July 15th, 2021 by Wired
LineStar Integrity Services was hacked around the same time as Colonial Pipeline, but radical transparency activists have brought the attack to light.
When ransomware hackers hit Colonial Pipeline last month and shut off the distribution of gas along...
Read Full Story »
Tags: cyberattacks, ransomware
Posted in: Cybersecurity
June 25th, 2021 by Function4
Function4's Clients to Benefit from
Early-Stage Partnership With
Cybersecurity Firm
SUGARLAND, TX -Function4, a
leading managed technology
services provider (MTSP), recently
announced that one of their earlystage strategic partners, Sentinel...
Read Full Story »
Tags: cyber security, cyberattacks, ransomware, vendor / partner relationships
Posted in: Press Release
June 18th, 2021 by Function4
Leading Managed Technology Services
Provider (MTSP) Alerts SMBs of
Compromised Data
SUGARLAND, TX - Function4 a leading
managed technology services
provider (MTSP), announced today
that the company proactively
monitors the Dark Web to keep...
Read Full Story »
Tags: cyber security, cyberattacks, dark web
Posted in: Press Release
June 10th, 2021 by Garrett Hollander
Because of the ongoing COVID-19 pandemic, more people are working remotely than ever before. On the one hand, productivity hasn't really suffered as there are a large number of cloud-based tools that make it possible to be just as productive outside...
Read Full Story »
Tags: COVID-19, cyberattacks, remote working, risk management
Posted in: Cybersecurity
June 7th, 2021 by Darcy Mekis
Cybersecurity is a growing concern for organizations all over the world. A single attack can lead to thousands or even millions in losses, and cybercriminals continue to come up with more sophisticated methods of attack. Ransomware and malware...
Read Full Story »
Tags: cyberattacks, data backup and recovery, email, ransomware, small & medium-sized businesses (SMB), tips & training
Posted in: Cybersecurity
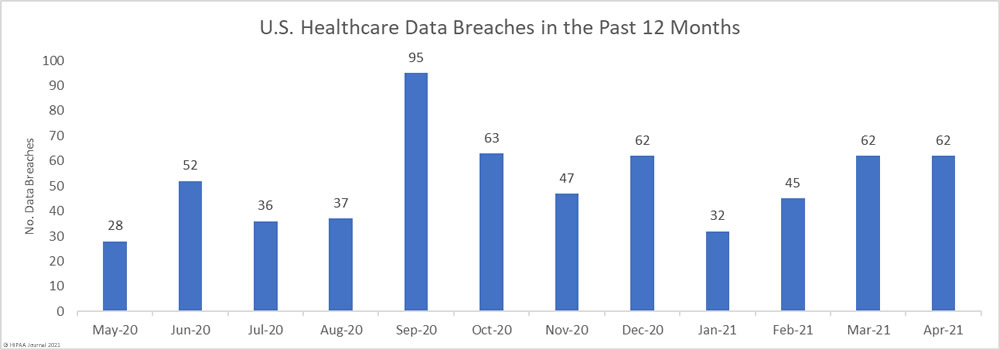
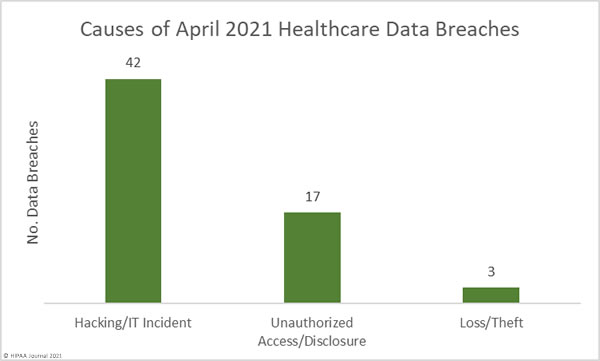
May 26th, 2021 by HIPAA Journal
April was another particularly bad month for healthcare data breaches with 62 reported breaches of 500 or – the same number as of March 2021. That is more than 2 reported healthcare data breaches every day, and well over the 12-month average of 51...
Read Full Story »
Tags: cyberattacks, healthcare, HIPAA / PHI, ransomware
Posted in: Cybersecurity
April 26th, 2021 by Function4
Function4 Helps Customers Protect
Their Precious Networks
SUGAR LAND, TX
Function4 a leading managed
technology services provider
(MTSP), proactively helps
businesses address the increased
threat of malware affecting small to
mid-sized...
Read Full Story »
Tags: cyber security, cyberattacks, ransomware
Posted in: Press Release
February 16th, 2021 by Darcy Mekis
Did you know your legacy phone system could be costing you business and eating away at profits? No matter what type of business you run, communication is critical. Voice calling is instrumental in customer service, new sales, and collaboration. However,...
Read Full Story »
Tags: cost reduction, cyberattacks, data backup and recovery, VoIP
Posted in: Phone Systems
January 19th, 2021 by Max Queen
As a small or medium-sized business (SMB) owner, you wear many hats. One of those responsibilities may be IT security, although you may have a nagging suspicion that your company is not adequately protected. With cyberattacks continuing to escalate,...
Read Full Story »
Tags: cost reduction, cyberattacks, data backup and recovery, risk management, small & medium-sized businesses (SMB)
Posted in: Business Technology
January 12th, 2021 by Max Queen
How much will it cost your company to recover following a data breach? New research from IBM Security paints a sobering picture, with costs increasing by 450,000 on average from 2019 to 2020. And here in the U.S., businesses can expect to pay even more...
Read Full Story »
Tags: cyberattacks, data analysis, data backup and recovery, managed IT, multifunction printers (MFP), risk management
Posted in: Cybersecurity
January 6th, 2021 by Max Queen
Iconic heists have made and destroyed fortunes. They make great scenes for exciting movie plots. Think of Butch Cassidy and his gang blowing up train tracks and fleeing on horseback with $50,000 in cash. Or consider a thief walking out of the Louvre...
Read Full Story »
Tags: cyberattacks, ransomware, risk management
Posted in: Cybersecurity
November 11th, 2020 by Ed Hoffmann
DARK WEB SCANNING: WHY IT IS IMPORTANT?
Have you heard of the dark web? It’s the hidden part of the internet where the illegal activity takes place online. The dark web has become a hotspot for criminals who want to sell your data. Fortunately, dark...
Read Full Story »
Tags: cyberattacks, Google, healthcare, risk management
Posted in: Cybersecurity
October 22nd, 2020 by Josh Chrisman / Kevin Box
When the COVID crises begin early in 2020 and offices started to reopen, many organizations scrambled to put policies and programs to help keep employees and customers safe. If you've recently walked into any public facility, you've probably experienced...
Read Full Story »
Tags: COVID-19, cyberattacks, GoSafe, healthcare
Posted in: Cybersecurity
August 5th, 2020 by Ed Hoffmann
Organizations today face an ever-increasing number of cyber threats. The rapid growth of criminal software development, coupled with the cybersecurity skills shortage, has also contributed to the rise in cyber-attacks.
The COVID-19 pandemic has had...
Read Full Story »
Tags: COVID-19, cyberattacks, email, ransomware, tips & training
Posted in: Cybersecurity
July 22nd, 2019 by Function4
Do you worry about a cybersecurity breach impacting your business? These threats to cybersecurity are increasingly common, as hackers become more sophisticated and bolder in their attacks. Data breaches are destructive to your customers and your company’s...
Read Full Story »
Tags: cyberattacks, data analysis, ransomware, risk management, tips & training
Posted in: Cybersecurity
April 29th, 2019 by Function4
With all of the responsibilities that come with small business ownership, it’s easy to neglect cybersecurity. However, the cost of a data breach is simply too high to ignore. A single data breach could destroy your company’s revenue and reputation —or...
Read Full Story »
Tags: cyberattacks, risk management, small & medium-sized businesses (SMB)
Posted in: Cybersecurity
April 3rd, 2019 by Function4
When you leave the office each evening, you probably lock the doors and set the security alarm. This seems obvious since you don’t want criminals breaking into your business. But do you treat cyberthreats with the same caution? After all, you probably...
Read Full Story »
Tags: cost reduction, cyberattacks, government agencies, risk management
Posted in: Cybersecurity
March 13th, 2019 by Function4
IT security issues are on every business leader's mind, or they should be. For every high profile cyberattack, there are thousands more that never make the headlines. Where does your company stand?
With small and midsize businesses (SMBs) now a favorite...
Read Full Story »
Tags: cyberattacks, managed IT, risk management, small & medium-sized businesses (SMB)
Posted in: Cybersecurity
February 25th, 2019 by Function4
Iconic heists have made and destroyed fortunes. They make great scenes for exciting movie plots. Think of Butch Cassidy and his gang blowing up train tracks and fleeing on horseback with $50,000 in cash. Or consider a thief walking out of the Louvre...
Read Full Story »
Tags: cyberattacks, email, risk management
Posted in: Cybersecurity
February 18th, 2019 by Brad Yocum
I began my career as a young 20-year-old in the mid-1990s working in the copy, print and imaging industry. At the time, office technology was just in its infancy. Creating a duplicate copy of an image was cutting edge. Sending pictures via fax was innovative....
Read Full Story »
Tags: cyberattacks, email, mobility, risk management
Posted in: Cybersecurity
February 13th, 2019 by Function4
Mass-scale AI-driven cyberattacks could be headed your way soon. Artificial intelligence (AI) is already effectively deployed as a way to detect malware and combat spam, so it stands to reason that AI will soon be a favored tool for hackers.
With AI...
Read Full Story »
Tags: cyberattacks, email, managed IT
Posted in: Cybersecurity
January 28th, 2019 by Function4
Data breaches are a company’s biggest fear.
If you own a company, the thought of someone stealing your data is probably enough to make you want to cut the cord and take your company offline. Of course, this isn’t practical in today’s economy, as computers...
Read Full Story »
Tags: cyberattacks, email, risk management, small & medium-sized businesses (SMB)
Posted in: Cybersecurity
December 17th, 2018 by Function4
The predictions were accurate—mobile workforce numbers continue to grow as companies realize the value of an agile staff with 24/7 access to business data. Here's why the most successful among these business leaders look to mobile device management to...
Read Full Story »
Tags: cyberattacks, mobility, remote working, risk management
Posted in: Business Technology
October 8th, 2018 by Function4
Social engineering has been around since the first traveling hucksters pitched miracle cures from the back of horse-drawn wagons. Today's social engineering schemes may be a little more sophisticated, but they have the same result—very embarrassed victims...
Read Full Story »
Tags: cyberattacks, email, managed IT, risk management, tips & training
Posted in: Cybersecurity
September 17th, 2018 by Function4
While most efforts to protect information have to do with stopping outside intruders and malicious attacks, information is vulnerable from the inside as well. Is yours protected?
Protection Through Your Document Management System
Document management...
Read Full Story »
Tags: cyberattacks, data backup and recovery, risk management
Posted in: Document Management
August 20th, 2018 by Function4
How much will it cost your company to recover following a data breach? New research from the Ponemon Institute and IBM paints a sobering picture, with costs increasing by 1.8% in 2017. And here in the U.S., businesses can expect to pay even more than...
Read Full Story »
Tags: cost reduction, cyberattacks, data backup and recovery, managed IT, multifunction printers (MFP), risk management
Posted in: Business Technology
July 9th, 2018 by Function4
A recent international survey by Check Point Software Technologies made it clear that businesses must step up their game when it comes to mobile device management. Their unsettling research of 850 firms revealed:
No business was left untouched—each...
Read Full Story »
Tags: cyberattacks, mobility, risk management
Posted in: Cybersecurity
June 11th, 2018 by Function4
With security breaches continuously on the rise, SMBs have been unable to escape the fallout. In fact, more than 60% of small businesses were the victim of some form of cybercrime in 2017. Since you would rather be in the 40% of companies who didn't...
Read Full Story »
Tags: cyberattacks, email, risk management, small & medium-sized businesses (SMB), tips & training
Posted in: Cybersecurity