Printer Security Vulnerabilities and What You Can Do About It!
August 10th, 2021 by Kevin Box


On April 29th, 2021, Cyber Criminals were able to hack the largest fuel pipeline in the U.S. because of one password floating around on the dark web, which an employee had previously used to access the organizations' network through a Virtual Private Network (VPN). According to a recent Bloomberg article, the compromised password was part of a batch of passwords leaked to the dark web. Bloomberg Article: June 2021
I wrote about another high-profile attack in my March 2019 article published on Function4.com titled Are Your Business Printers Vulnerable To Hackers? My report outlined the fundamentals behind the Target attack in December 2013 in which Target's network was breached with stolen credentials through an HVAC sub-contractor working for Target. Both attacks cost each organization millions of dollars and, in the case of Target, well over $200 million in legal fees alone. Both security breaches were different in deployment but similar in that cybercriminals exploited unknown vulnerabilities inside each organization's network. These breaches further underscore the fine line between a secure network and a network vulnerable to an attack. Networks are only as strong as their weakest link, which is often the endpoint.
Cyberattacks are Growing!
Cyberattacks have grown exponentially since the Pandemic hit back in early 2020. Estimates show that IT Security spend will top $6 Trillion in 2021, and IDC states that 70% of the breaches will begin at the endpoint. According to CSO online, attacks on IoT (Internet of Things) devices tripled in the first half of 2019 and will continue to grow if IoT remains vulnerable. The definition of an endpoint is any node connected to the network, which includes computers, Nest-type thermostats, Ring doorbells, security cameras, and last, but certainly the most ubiquitous are printers.
Some of the biggest unknowns on any network are printers which organizations often ignore. Printers come out-of-the-box as unlocked capsules that can give cybercriminals a backdoor into your network if not properly remediated.

Once deployed, printers are, for the most part, untouched. Meaning if it isn't broke, don't fix it. Organizations will focus primarily on securing computers with anti-virus protections like Webroot or McAfee anti-virus but completely ignore securing printers even though printers are merely a computer with a Hard Drive, a BIOS, a user interface, etc.
So, why aren't organizations taking securing printers seriously?
The simple answer is they may not know how vulnerable printers are or believe printers aren't vulnerable to attacks because it sits behind a firewall. The truth is that firewalls are only one layer of security and not enough to protect printers from being hacked.
Juan Baskerville, a Technical Consultant with HP’s South Central US Division, counsels HP clients regularly about printer security and believes some of his clients have misconceptions about how safe printers are behind the corporate firewall. In a recent meeting with Juan in preparation to write this piece, he mentioned that “In selling printers and talking about security, one of the biggest myths that customers tell us is their printers are protected simply by putting them behind the firewall or that printers aren’t vulnerable to cyber-attacks. Many think that if the printer is on the corporate network, all threats have been neutralized. This idea assumes that punching through the firewall is the only way to penetrate a network and ignores a lot of other scenarios where the firewall is just bypassed-like phishing emails or attacks based on physical access to the device. I think anyone who takes security seriously understands that no network is absolutely secure. The best we can hope for is to protect the devices and data on the network, detect threats as they come, and recover from the damage caused as quickly as possible.”
Juan’s statement further underscores the importance of having multiple security layers on the network and helps strengthen the case that many organizations don't realize how easy it is for cybercriminals to access printers on the network behind the firewall. Every printer connected to your network has an IP address, which means bad actors could potentially find the IP address and connect to the printer from the outside. If you overlook printer security, you run the risk of that printer being hacked into and the settings changed for the hacker's benefit.
This means the hacker could access scanned documents or gain access to the Active Directory on the device and pose as anyone credentialed to use the printer. If they can find the directory and choose a user, they can get right into your network, which means they bypass the firewall and have direct access to the network.
If you were to do a Google search on "How to hack a printer" or "hacking printers," what comes up is a treasure trove of ways to hack a printer. There's even an entire Wikipedia page dedicated to hacking printers. So, you get the idea that hacking a printer is as easy as a Google search.
So, what can you do about it? The answer is easier than you may think!
According to Hackingpassion.com, there are four primary ways to secure your printers.
- Change the default password of your printer – This seems easy enough; however, most organizations will ignore this simple step. Printers come out of the box with a default password set by the manufacturer and are widely known on the dark web.
- Check the printer’s IP Address – Printers may come with an external IP address, so it's best to switch it to an internal one. You can also limit access to a specific LAN or Subnet for added protection.
- Secure Your Ports – You should disable all unused ports on your printer. Print jobs are sent to the print queue through various protocols such as SMTP, FTP, Telnet, etc., so hackers can also use open ports to hack into the printer. If you don't use the port, disabling it will close off the hacker's ability to enter through that port.
- Apply the latest firmware updates – Firmware updates are needed periodically because manufacturers will develop scripts and patches anytime it finds vulnerabilities within the printer's operating system. Downloading the newest version of firmware will decrease security occurrences and help make your printers more secure.

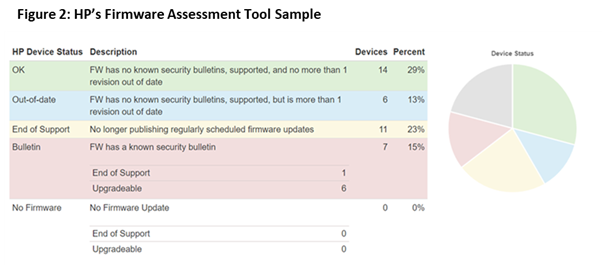
You can also use firmware tools on your fleet to see which devices are behind on firmware updates. For example, HP has an excellent Firmware Assessment Tool that can tell you if any of your HP printers are behind on firmware updates or which devices have known security bulletins that need to be addressed. This can help you evaluate the security health of your printers to see what changes need to be made in real-time to ensure your printer fleet is up to date on firmware. Again, function4 can perform this assessment for your organization at no charge, so reach out to us if we can help.
Security is about layers. The more layers you have reduces the likelihood that your organization will be hit with a cyber-attack. It doesn't guarantee that hackers can't penetrate your network, however, it can help decreases their chances. Taking a few steps upfront with your printers can help give you an additional layer of security protection over your printer fleet, which could pay dividends in stopping future security breaches.
Kevin Box is the Director of Managed Print Services for Function4 Headquartered in Sugar Land, TX and is HP Sales Certified in Advanced Endpoint Security. He can be reached directly by email at kbox@function-4.com. Follow him on LinkedIn at LinkedIn/Kevin Box
Posted in: Cybersecurity

