Cybersecurity Trends to Know in 2020 & How to Protect Your Business
August 5th, 2020 by Ed Hoffmann
Organizations today face an ever-increasing number of cyber threats. The rapid growth of criminal software development, coupled with the cybersecurity skills shortage, has also contributed to the rise in cyber-attacks.
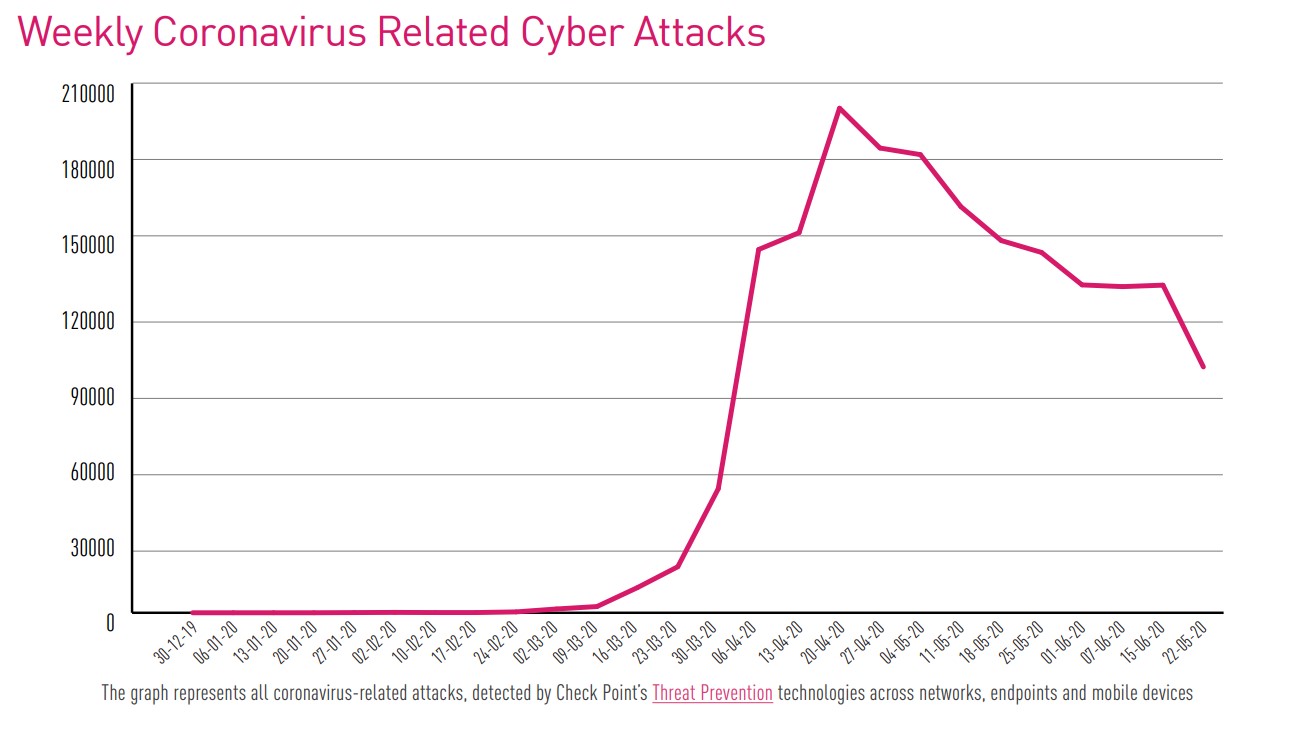
The COVID-19 pandemic has had a dramatic effect on virtually every aspect of life and was, without doubt, the most influential event in the first half of 2020. There were substantial repercussions in the cyber arena as well. A variety of actors with diverse motivations – criminal, political, or espionage – used concerns about COVID-19 and related themes to target a whole new set of victims.
The “new normal” has created challenges, for sure. However, it has also created opportunities. Infrastructure changes made by companies to allow remote access have also required threat actors to adapt to a hybrid world that integrates cloud technologies.
Trending Cyber Threats
We are used to the regulars in terms of common threats (malware, ransomware, phishing attempts, brute-force attacks, etc.), here are some trending threats to know in 2020:
- Double Extortion - Ransomware actors have adopted a new strategy; in addition to making the victim’s files inaccessible, they now exfiltrate large quantities of data before its encryption in the final stage of the attack. Victims who refuse payment demands find their most sensitive data publicly displayed on dedicated websites.
- Mobile - Cybercriminals have been seeking new infection vectors in the mobile world, changing, and improving their techniques to avoid detection in places such as the official application stores. In one innovative attack, threat actors used a large international corporation’s Mobile Device Management (MDM) system to distribute malware to more thanv75% of its managed mobile devices.
- Cloud - Industries were required to make rapid infrastructure adjustments to secure their production when working remotely. In many cases, this would not have been possible without cloud technologies. However, it also exposed more misconfigured or simply unprotected assets to the internet. Also, for the first time, alarming vulnerabilities were revealed in Microsoft Azure infrastructure that could enable invaders to escape VM infrastructure and compromise other customers. Data management has become more critical than ever.
There is a big misconception about cybersecurity. Business owners think that once they have hired a managed service provider (TSP) to maintain their security, or installed a firewall and antivirus, they are completely protected and no longer at risk. However, the most significant threat to an organization’s information security is the inaction of employees.
What this means is that human error is a significant point of weakness. Reports have shown that as much as 90% of cyberattacks are caused by human behavior. With that said, businesses must employ some cybersecurity training for team members to understand their responsibilities, learn how to protect sensitive information, and recognize signs of malicious threats.
As a security provider, Function4 recommends intelligent profiling and alerting technology to enforce end-to-end security policies. If you do not have those tools or strategy in place, here are a few tips to help secure your environment now:
Avoiding Phishing and Social Engineering Attacks
What should an organization do if they have been involved in a phishing attack?
- Never click! If end-users feel like something is not quite right, they should never click on a link or attachment or give out sensitive information.
- Tell IT or your MSP. Informing the right person or department promptly, is critical in preventing a phishing scam from spreading company wide. Always encourage your clients to ask you to investigate or provide additional steps.
Access, Passwords, and Connection
Employees should be using best practices when it comes to passwords they are creating, especially for passwords used to access IT environments. In general, passwords:
- Should be unique to each app/site, at least eight characters, contain letters, and special characters
- Stay away from obvious information like names and birthdays.
- Change and update passwords every six months. A password manager—like 1Password—can help with all of this.
This may be less obvious to employees, but they should be wary of network connections used outside of their home or work. Even if data on their device is encrypted, it is not necessary that a connected network transfers that data in an encrypted format, which opens the door to many different vulnerabilities. Plus, public networks may be tapped, which puts all data exchanged on that network at risk. Encourage end users only to use trusted network connections or secure the connection with appropriate VPN settings.
Device Security
We are living in a time where it is fashionable to Bring Your Own Device (BYOD), meaning more and more mobile or personal devices are entering the workplace, connecting to the corporate network, and accessing company data. This creates more entry points for threats to happen, so all mobile devices must also be securely connected to the corporate network and always in the employee’s possession.
Physical Security
Cyberthreats are not the only risks employees need to be mindful of. Physical security also plays a role in keeping sensitive information protected. How often and easily do you mistakenly leave a mobile device or computer unattended? It happens to all of us. But, if someone were to swipe an employee’s unattended phone or log in to their computer, all their data would immediately be at risk.
Here are how your employees can increase their physical security in and out of the office:
- Lock all devices. Get in the habit of doing this every time you leave your desk. For Windows users, press and hold the Windows key, then press the “L” key. For Mac users, press Control + Shift + Eject (or the Power key) at the same time.
- Lock your docs. Store all your documents in a locked cabinet, rather than leaving sensitive information hanging around your desk. Before leaving for the day, stow critical documents into a safe or locked cabinet.
- Properly discard info. When you are throwing away or getting rid of documents and files, make sure you are shredding them and discarding them appropriately.
Need more cybersecurity info? We have got you covered! Register for Function4’s Webinar “Cybersecurity Trends to Know in 2020” where we will take a deeper dive into what’s happening now and learn how to protect your business in the future with the proper security strategy.
Ed Hoffmann, Managed Services Development, Function4 LLC
Posted in: Cybersecurity

